Převzato z http://www.ogametips.com/25/building-defenses, později v případě zájmu spoluhráčů tento článek přeložím do češtiny.
Building Defenses
Prev: Viewing your Galaxy uses Deuterium | Next: Like space strategy games? Try OGame
Published: Apr 19, 03:29 PM by: Robert ~ Voidhawk
There is more information on about Building Defenses and using SpeedSim here.
This is a reprint of the post found here at the oGame Forums
Building Defenses
There is a fair bit of debate over whether you should build defense or fleet and in what combo but if you are going to build a defense then this is what I have done.
Laser/Energy Weapons
* Ignore missile launchers, cruisers get rapid fire to early and you need the metal to grow mines.
* Use missile launchers in the later defenses. Early on, cruisers can wipe them out easily. But once you hit the bigger fights, they are a cheap source of cannon fodder. 5 Missile Launchers per 1 small laser.
* Small Lasers become your cannon fodder (some ships get RF but they wont appear to early so it gives you a bit of time to get started)
* Build 1 Heavy Laser per 4 Small lasers. (Only bombers and death stars get RF so they become your anti RF midgame).
* Build 1 ion cannon per 12 Small lasers. (ion cannons have high shields which helps everything else survive)
* Build 1 Gauss Cannon per 30 small lasers (first big gun and useful vs cruisers and maybe low numbers of battleships, but will struggle vs destroyers)
* Build 1 Plasma Cannon per 100 small lasers (This is the weapon your going to rely on to fend off those war attacks where someone just wants to bash you rather than steal some cheap resources)
Shields
* Small shield after 20 Light lasers
* Large Shield after 100 small lasers
Overview
So by the time you hit 100 small lasers, you have:
* Small Shield
* Large Shield
* 25 Heavy Lasers
* 8 or 9 Ion Cannons
* 3 or 4 Gauss Cannons
* 1 Plasma Cannon
At this point, the odds of someone hitting the plasma cannon is 1:136 but it will be dishing out fatal damage steadily.
From what I can read no weapon will survive on its own in all situations. You need enough small stuff to make it unlikely that they will hit you big guns. Enough big guns to actually destroy their ships (rather than scratching all of them a little, but destroying none). Enough shields to prevent their damage from destroying you defenses to quickly. The combination will be different for everyone and will be affected by what you are facing.
Missile Silos
Build them as well – when you consider interplanetary missiles a threat.
The whole point of a defense is to make it unprofitable for someone to attack. Low resources at home and enough defense to deter the attack. If you ever have to use it its probably not big enough. Silos 2 will give you 10 anti-ballistic missiles. I would think this is plenty for most of the game (except maybe later in a war. Anti-Ballistic Missiles are cheaper to build than Interplanetary ones.
Misc.
A defense is a money sink. You need to keep adding to it as you produce more, but should never really need to use it. Its the attacks that look at you, say “to big/not worth it” and go elsewhere that you are really trying to catch. If you want to see what ratio you should use for mines vs defenses then read the article.
Another suggestion: If your going to use defenses then keep your resources low. Ship them away or spend them. It doesn’t really matter but dont leave large numbers lying around. It will just draw an attack that you cant defend against, and you will end up losing your defenses and your resources.
This does not take into account using fleets as defense. That is another topic for another day.
UPDATE: Added some advice on using Missile Launchers.
sobota 25. srpna 2007
OGame - Energie
Text je převzán z OGame Tips Strategy Guide – http://www.ogametips.com/, časem ho snad i přeložím pokud budou mít spoluhráči zájem....
Providing Power There are three ways to get power in OGame. The first (and primary) is the Solar Plant. The second is the Fusion Plant, and finally there are Solar Satellites.
The Solar Plant is a building created on your planet. It takes up one field per level of Solar Plant on the planet, and produces a fixed rate of energy per level. They do not use any resources to produce energy, nor is the amount produced dependent on the distance from the sun.
The Fusion Plant (which requires a Level 5 Deuterium Synthesizer) uses your Deuterium to produce Energy. The warmer the planet, the more energy produced per Deuterium. However, the colder your planet, the more Deuterium a Deuterium Synthesize produces. This source of power can be detrimental to your Deuterium supplies if your Deuterium Synthesizers are not producing well. You should balance out your power plants using a proper mix of Solar Plants and Deuterium Synthesizers.
The Solar Satellites produce anywhere from 1 to 50 energy per satellite, depending on the maximum temperature of your planet. The warmer the planet, the more energy produced. Each Solar Satellite costs you 2000 Crystal and 500 Deuterium.
TIP:
Solar Satellites are one of the first items destroyed by an attacking fleet. Having excessive Solar Satellites can lead to a raid, since the attacker can harvest the debris left by the destruction of the satellites (see Recycling Debris for more details).
Solar Satellite Formula:
You can use the following formula to find out how much energy a Solar Satellite produces on a given planet.
(MaxTemp/4)+20
To find your MaxTemp, go to the “Overview” section for each planet and look at the Temperature field. It should look something like this:
Temperature approx. 1°C to 41 °C
In the above example, 41 °C is the MaxTemp for the planet.
Providing Power There are three ways to get power in OGame. The first (and primary) is the Solar Plant. The second is the Fusion Plant, and finally there are Solar Satellites.
The Solar Plant is a building created on your planet. It takes up one field per level of Solar Plant on the planet, and produces a fixed rate of energy per level. They do not use any resources to produce energy, nor is the amount produced dependent on the distance from the sun.
The Fusion Plant (which requires a Level 5 Deuterium Synthesizer) uses your Deuterium to produce Energy. The warmer the planet, the more energy produced per Deuterium. However, the colder your planet, the more Deuterium a Deuterium Synthesize produces. This source of power can be detrimental to your Deuterium supplies if your Deuterium Synthesizers are not producing well. You should balance out your power plants using a proper mix of Solar Plants and Deuterium Synthesizers.
The Solar Satellites produce anywhere from 1 to 50 energy per satellite, depending on the maximum temperature of your planet. The warmer the planet, the more energy produced. Each Solar Satellite costs you 2000 Crystal and 500 Deuterium.
TIP:
Solar Satellites are one of the first items destroyed by an attacking fleet. Having excessive Solar Satellites can lead to a raid, since the attacker can harvest the debris left by the destruction of the satellites (see Recycling Debris for more details).
Solar Satellite Formula:
You can use the following formula to find out how much energy a Solar Satellite produces on a given planet.
(MaxTemp/4)+20
To find your MaxTemp, go to the “Overview” section for each planet and look at the Temperature field. It should look something like this:
Temperature approx. 1°C to 41 °C
In the above example, 41 °C is the MaxTemp for the planet.
pátek 10. srpna 2007
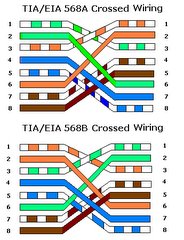
Sítě - Otázky
Základní principy přenosu dat
- Jaké nepříznivé vlivy působí na signál přenášený médiem ? Jakými fyzikálními vlastnostmi média (metalického, optického) jsou ovlivněny ? Lze je zcela eliminovat ?
- Jaký je rozdíl mezi synchronním a asynchronním sériovém přenosem ?
- Vysvětlete pojmy simplex, half-duplex a duplex.
Topologie sítí. Přenosová média. Metody sdílení přenosového média.
- Jaké topologie počítačových sítí znáte ? Jaké jsou výhody a nevýhody každé z nich ?
- Jaké přenosová média znáte ? Jaké jsou výhody a nevýhody každého z nich ? Jaké médium se dnes nejčastěji používá v lokálních sítích ?
- Co znamená označení média UTP5 ?
- Jaké dva základní typy optických vláken rozlišujeme ? Jaké jsou výhody a nevýhody každého typu ?
- Vysvětlete pojem "strukturovaná kabeláž".
- Jakými metodami lze sdílet přenosové médium, které poskytuje šířku pásma dovolující přenášet současně více signálů ? Vysvětlete základní princip těchto metod.
Metody sdílení přenosového kanálu
- Proč je v lokálních sítích třeba implementovat přístupovou metodu ke společnému kanálu ? Co má přístupová metoda za úkol ?
- Vysvětlete rozdíl mezi deterministickými a nedeterministickými přístupovými metodami a jejich výhody a nevýhody.
- Jaké konkrétní deterministické a nedeterministické přístupové metody znáte ?
- Vysvětlete princip metod CSMA/CD a Token Passing.
Referenční model ISO-OSI
- Vysvětlete výhody vrstvené architektury komunikujících systémů. Jak probíhá komunikace mezi vrstvami ?
- Jaké konkrétní vrstvy definuje referenční model ISO OSI a co je úkolem každé z vrstev ?
- Vysvětlete pojem "enkapsulace".
- Vysvětlete rozdíly mezi komunikací se spojením a beze spojení.
Propojování sítí, aktivní prvky a jejich principy.
- Jaké prvky pro propojování sítí znáte ? Kdy použijete který z nich ? Na kterých vrstvách referenčního modelu ISO-OSI pracují ?
- Popište princip funkce rozbočovače (hub), přepínače (switch) a směrovače (router).
- V čem spočívá problém se smyčkami při použití transparentních mostů (přepínačů) ? Jak se odstraňuje ? Jakým způsobem může administrátor vzniklou aktivní topologii ovlivnit a proč to může být užitečné ?
- Proč pro propojování různých typů lokálních sítí nevystačíme s přepínači, ale potřebujeme router ? Proč často potřebujeme router i pro propojení sítí stejného typu ?
Standardy IEEE 802. Ethernet. Přepínané sítě, virtuální sítě.
- Jaké úkoly plní vrstva LLC a MAC z doporučení IEEE 802 ?
- Jaký je formát MAC adres ? Jak vypadá MAC adresa označující broadcast ?
- Co definují doporučení IEEE 802.3, 802.5 a 802.11 ?
- Popište základní charakteristiky sítě Ethernet (možné topologie + dosah, používané médium a aktivní prvky, přístupová metoda, přenosové rychlosti).
- Co znamenají zkratky 10BaseF, 100BaseT a 1000BaseSX ?
- Jaký je rozdíl mezi half-duplex a full-duplex Ethernetem ? Na jakých aktivních prvcích musí být síť Ethernet založena, aby mohla být provozována ve full-duplex režimu ?
- Jak vypadá rámec Ethernetu ?
- Vysvětlete funkci přepínače (switch). Jak se liší přepínač od mostu ?
- Vysvětlete, co znamená virtuální síť (VLAN). Jaká je výhoda jejich nasazení ? Jaké aktivní prvky pro nasazení VLAN potřebujete ?
Přenosové protokoly Internetu - protokolová rodina TCP/IP
- Jaké protokoly se v Internetu používají na 3. a 4. vrstvě OSI RM ?
- Srovnejte vrstvený model architektury TCP/IP s ISO OSI RM.
- Jaká je délka a struktura adresy protokolu IP ? Co znamenají třídy adres ? Co jsou beztřídní adresy a k čemu se u nich používá maska podsítě (subnet mask) ?
- Co jsou privátní adresy a k čemu se používají ? Kdo je přiděluje ? Uveďte aspoň jeden z rozsahů, který můžete použít jako privátní adresy.
- Co reprezentují IP adresy 255.255.255.255 a 127.0.0.1 ?
- Jak se formálně označí určitá IP (pod)síť jako celek ?
- Jak vypadá adresa broadcastu pro určitou konkrétní IP (pod)síť ?
- Proč se používá podsíťování (subnetting) a v čem spočívá jeho princip ?
- K čemu slouží překlad adres (NAT) , jaký je jeho princip a na jakém síťovém prvku jej lze realizovat ?
- Na jakém principu lze pomocí NAT za jedinou veřejnou IP adresu "ukrýt" větší množství vnitřních adres ?
- Na které vrstvě pracuje IP protokol ? Co je jeho úkolem ?
- Vysvětlete úkol a princip činnosti protokolu ARP.
- Vysvětlete, k čemu se používá protokol ICMP. Uvěďte alespoň několik typů ICMP zpráv vždy s příkladem konkrétní situace, za které se generují (vždy rovněž udejte, kdo bude zprávu generovat).
- K čemu se používá příkaz traceroute implementovaný ve většině OS ? Vysvětlete princip jeho funkce.
- Jaké protokoly se v Internetu používají na 4. vrstvě ? Jaký je mezi nimi rozdíl ? K jakým účelům je který z nich výhodnější ?
- Popište význam položek hlavičky UDP.
- Popište význam položek hlavičky TCP.
- K čemu se u protokolů UDP a TCP používají porty ? Proč nestačí cílový port, ale pracuje se i se zdrojovým portem ?
- Popište proceduru navázání a uzavření spojení u protokolu TCP.
- Popište výměnu dat během TCP spojení včetně řízení toku (flow control). Zaměřte se na položky Sequence number, Acknowledgement number a Window v hlavičce TCP segmentu.
Směrování a směrovací algoritmy
- Vysvětlete pojem směrování. Které aktivní prvky se směrováním paketů zabývají ?
- Vysvětlete pojem směrovací tabulka. Jaké položky (sloupce) byste očekávali v jejich jednotlivých záznamech (řádcích) ?
- Vysvětlete pojem implicitní cesty (default route).
- Jaký je rozdíl mezi statickým a dynamickým směrováním ?
- Vysvětlete princip, výhody a nevýhody hierarchického směrování.
- Vysvětlete pojem směrovací protokol.
- Do jakých dvou základních kategorií směrovací protokoly (algoritmy) dělíme ?
- Vysvětlete princip směrovacích algoritmů na bázi vektorů vzdáleností (distance vector).
- Vysvětlete princip směrovacích algoritmů na bázi stavů spojů (link state).
- Srovnejte výhody a nevýhody směrovacích algoritmů tříd distance vector a link state.
- Uveďte reprezentanty směrovacích algoritmů tříd distance vector a link state v prostředí TCP/IP.
Protokoly služeb Internetu
- K čemu se používá protokol Telnet ? Který port služba používá ?
- K čemu slouží protokol FTP ? V čem spočívají jeho bezpečnosní rizika ?
- Jaké dva typy kanálů se při práci FTP vytváří a jaké porty se k tomu používají ? Kterými příkazy protokolu se zajistí přečtení a uložení souboru ? K čemu slouží příkaz PORT ? Jak se přenáší obsah adresáře (příkaz list) ?
- K čemu se používá protokol TFTP a jak se technicky liší od FTP ?
- Jaké protokoly se používají pro odesílání zpráv elektronické pošty a jaké pro vzdálené vyzvedávání zpráv z poštovních přihrádek ? Jaký protokol transportní vrstvy se při tom využívá ?
- Jaká je úroveň autentizace a šifrování v běžných protokolech pro odesílání a stahování pošty ?
- Co je to URL ? Jaká je obecná struktura URL ?
- Jaký protokol se používá pro čtení WWW stránek (HTML) ? Nad jakým transportním protokolem a se kterým číslem portu pracuje ?
- Vysvětlete, proč odpověď WWW serveru na žádost o určité URL obsahuje nejen obsah samotného zdroje, ale i hlavičku. Uveďte příklady údajů, které se mohou v hlavičce vyskytovat.
- Vysvětlete, proč i HTTP požadavek obsahuje hlavičku. Uveďte příklady údajů, které mohou být uvedeny v hlavičce požadavku HTTP.
- Jak se realizuje autentizace uživatelů při přístup na WWW stránky ?
- Co jsou a k čemu lze použít Cookies ?
- Jak lze zajistit šifrování a autentizaci při přenosu WWW stránek ?
- Vysvětlete, k čemu se používá protokol DHCP. Jaké parametry lze jeho prostřednictvím předat ? Jaká je výhoda oproti statické konfiguraci stanice ? Popište sekvenci zpráv protokolu během přidělování IP adresy dynamicky konfigurovatelné stanici.
- Proč je problémem,když DHCP server není na stejném segmentu jako klienti ? Jak lze tuto situaci řešit ?
Bezpečnost sítí
- Definujte pojmy utajení, autentizace a integrita.
- Čím se liší symetrický a asymetrický kryptografický systém ? Jaké jsou jejich výhody a nevýhody ?
- K čemu lze použít soukromá a veřejný klíč ?
- Jak lze realizovat autentizaci v symetrickém a asymetrickém systému ?
- K čemu slouží certifikační autorita ?
- Jak lze ověřit integritu zprávy ?
- Jaké jsou výhody a nevýhody realizace bezpečnosti na 2., 3. 4. a 7. vrstvě ISO OSI RM ?
- Vysvětlete, v čem spočívá filtrace provozu na základě bezestavové inspekce paketů. Proč se nazývá bezestavová a v čem jsou její omezení oproti plnohodnotnému stavovému firewallu ? V čem je výhodnější ?
- Co jsou reflexivní ACL ?
- Proč se někdy tvrdívá. že NAT zvyšuje bezpečnost vnitřní sítě ?
- Vysvětlete pojem virtuální privátní sítě a tunelu.
- Jaká bezpečnostní rizika plynou z dynamických směrovacích protokolů ?
- Jaká bezpečnostní rizika plynou z protokolu ARP ?
- Jaké bezpečnostní rizika a ochranné mechanismy znáte v souvislosti s přepínači ?
Rádiové sítě, IEEE 802.11
- Co znamená zkratka WiFi a v jakém doporučení IEEE jsou rádiové sítě ve volném pásmu definovány ?
- V jakých dvou nelicencovaných pásmech mohou sítě WiFi pracovat ?
*BAT - Test sitovky
Jednoduchý test sítové karty *.bat souborem:
SET CONNECT=funguje
PING 127.0.0.1 | FIND "TTL=">NUL
IF ERRORLEVEL 1 SET CONNECT=nefunguje
ECHO sitove rozhrani %CONNECT% spravne
SET CONNECT=funguje
PING 127.0.0.1 | FIND "TTL=">NUL
IF ERRORLEVEL 1 SET CONNECT=nefunguje
ECHO sitove rozhrani %CONNECT% spravne
pondělí 6. srpna 2007
CCNA - Final Exam v3.1
CCNA2 Final Exam v3.1
Which of the following could describe the devices labeled "?" in the graphic? (Choose three.)
**DCE
**CSU/DSU
LAN switch
**modem
hub
-------------------------------------------------
Router A and Router B have been correctly configured to use RIP as a dynamic routing protocol and all intefaces on Router A and Router B are reporting "interface is up, line protocol is up" status. RIP is then configured on Router C using the following commands:
RouterC(config)# router rip
RouterC(config-router)# network 192.168.4.0
RouterC(config-router)# network 172.16.0.0
If no additional routing is configured on Router A, Router B, and Router C, what will be the result?
**Networks 192.168.12.0/24, 192.168.4.0/24, and 172.16.0.0/16 will be unreachable from Router A.
Router A will have no knowledge of network 192.168.12.0/24, but will have routes to networks 192.168.4.0/24 and 172.16.0.0/16.
All networks shown in the graphic will be reachable by Router A, Router B, and Router C.
Networks 192.168.4.0/24 and 172.16.0.0/16 will be unreachable from Router A and Router B.
--------------------------------------------------------
The following access list has been correctly applied to a router interface:
access-list 52 deny 172.30.65.52
access-list 52 permit any
Which of the following statements are true about this ACL? (Choose three.)
This is an invalid ACL because the wildcard mask is missing from the command.
**A wildcard mask of 0.0.0.0 is assumed for 172.30.65.52.
This is an extended IP access list.
**All traffic from 172.30.65.51 will be permitted.
**This is a standard IP access list.
---------------------------------------------------------
Refer to the graphic. Assuming default metrics are used and the network is fully converged, which path will the IGRP routing protocol use to send a packet from Router A to Router F?
A, D, E, F
**A, B, D, E, F
A, C, D, E, G, F
A, B, D, E, G, F
---------------------------------------------------------
Neither router in the graphic has a host table or DNS available. The interfaces and passwords have been correctly configured. Which of the following commands will initiate a Telnet session? (Choose two.)
ATL> connect CHI
ATL> telnet CHI
**ATL# 192.168.4.2
ATL# connect ATL
**CHI# telnet 192.168.4.1
CHI# telnet ATL
--------------------------------------------------------
What will occur if the command service password-encryption is entered on a router? (Choose two).
It will allow only the user EXEC mode password to be encrypted.
It will set an MD5 hashing algorithm on all unencrypted passwords.
**It will apply a weak encryption to all unencrypted passwords.
It will set the enable secret password to be encrypted.
It will apply an MD5 hashing algorithm to encrypt the console and telnet passwords.
**It will configure the user EXEC mode, telnet, and enable passwords as encrypted.
---------------------------------------------------------
A network administrator must configure a serial interface with an IP address. The configuration must also identify the remote site to which the interface is connected. Which set of commands will meet these requirements?
Chicago(config)# description San Jose T1
Chicago(config)# interface serial0/0
Chicago(config-if)# ip address 192.168.204.9 255.255.255.252
**Chicago(config)# interface serial0/0
**Chicago(config-if)# ip address 192.168.204.9 255.255.255.252
**Chicago(config-if)# description San Jose T1
Chicago(config)# interface serial0/0
Chicago(config-if)# ip address 192.168.204.9 netmask 255.255.255.252
Chicago(config-if)# description San Jose T1
Chicago(config)# interface serial0/0
Chicago(config-if)# ip address 192.168.204.9 255.255.255.252
Chicago(config-if)# remote site San Jose T1
Chicago(config)# interface serial0/0
Chicago(config-if)# ip address 192.168.204.9 255.255.255.252
Chicago(config-if)# interface description San Jose T1
-----------------------------------------------------
A network administrator has enabled RIP on routers B and C in the network diagram. Which of the following commands will prevent RIP updates from being sent to Router A?
A(config)# router rip
A(config-router)# passive-interface S0/0
B(config)# router rip
B(config-router)# network 192.168.25.48
B(config-router)# network 192.168.25.64
A(config)# router rip
A(config-router)# no network 192.168.25.32
**B(config)# router rip
**B(config-router)# passive-interface S0/0
A(config)# no router rip
-----------------------------------------------------
Which of the following describe Telnet on a router? (Choose two.)
**Simultaneous incoming Telnet sessions can be hosted by a router.
Telnet is the most basic testing mechanism available.
A Telnet session can only be initiated in privileged EXEC mode.
**Five separate Telnet lines are specified by the configuration line vty 0 4.
Telnet is classified as a network layer protocol.
--------------------------------------------------
Which commands will show the status and IP address of all interfaces on a router? (Choose two.)
**show protocols
show ip protocols
show version
**show interfaces
show ip ports
---------------------------------------------------
Which router command will generate the router output shown in the graphic?
show arp
show protocols
show interface FastEthernet0/0
show interfaces
**show hardware
---------------------------------------------------
Which of the following are valid boot system commands? (Choose two.)
Router(config)# boot system ram
**Router(config)# boot system rom
Router(config)# boot system IOS flash
Router(config)# boot system flash c2600-d-mz.121-3 192.168.10.5
**Router(config)# boot system tftp c1700-l-mz.131-2 172.16.24.7
---------------------------------------------------
During initial router bootup the following line appears:
"NVRAM invalid, possibly due to write erase."
What are two possible reasons for this result? (Choose two.)
The startup-config file was not saved to RAM before reboot.
The IOS has been erased.
**The router has not been configured.
**The startup-config file cannot be located.
The router will not enter initial configuration dialog.
--------------------------------------------------
While planning an IOS upgrade, the administrator issues the show version command. Based on the output in the graphic, what is the current IOS boot location?
RAM
**NVRAM
Flash
ROM
--------------------------------------------------
Which statements are true regarding setup mode? (Choose three.)
Press Ctrl-z to terminate setup mode.
**Enter a question mark (?) for help at any point.
Press Spacebar to accept the default settings.
Use setup mode to enter complex protocol features.
**Press Enter to accept the default settings.
**Press Ctrl-c to abort configuration dialog.
--------------------------------------------------
Which router components and operations are correctly described? (Choose two.)
ROM - stores the backup configuration file
RAM - loads the operating system
**NVRAM - stores the configuration file
Flash - executes diagnostics at bootup
**POST - runs diagnostics on hardware modules
DRAM - loads the bootstrap
--------------------------------------------------
access-list 199 deny tcp 178.15.0.0 0.0.255.255 any eq 23
access-list 199 permit ip any any
Assuming this ACL is correctly applied to a router interface, which statements describe traffic on the network? (Choose two.)
All FTP traffic from network 178.15.0.0 will be permitted.
**All Telnet traffic destined for network 178.15.0.0 will be denied.
Telnet and FTP will be permitted from all hosts on network 178.15.0.0 to any destination.
**Telnet will not be permitted from any hosts on network 178.15.0.0 to any destination.
Telnet will not be permitted to any host on network 178.15.0.0 from any destination.
------------------------------------------------------
Refer to the graphic. Communication is needed between the LAN connected to the fa0/0 interface of the Kansas router and the fa0/0 interface of the Maine router. All hosts on those LANs also need connectivity to the Internet. Which commands will allow this communication? (Choose three).
**Kansas(config)# ip route 192.168.6.0 255.255.255.0 172.18.64.2
Kansas(config)# ip route 192.168.6.0 255.255.255.0 s0/1
**Kansas(config)# ip route 0.0.0.0 0.0.0.0 s0/1
Maine(config)# ip route 192.168.6.0 255.255.255.0 172.18.64.1
**Maine(config)# ip route 0.0.0.0 0.0.0.0 s0/1
Maine(config)# ip route 172.16.32.0 255.255.255.0 172.18.64.2
-------------------------------------------------------
Due to a security violation, the router passwords must be changed. What information can be learned from the following configuration entries? (Choose two.)
Router(config)# line vty 0 3
Router(config-line)# password c13c0
Router(config-line)# login
The entries specify three Telnet lines for remote access.
**The entries specify four Telnet lines for remote access.
The entries set the console and Telnet password to "c13c0".
Telnet access will be denied because the Telnet configuration is incomplete.
**Access will be permitted for Telnet using "c13c0" as the password.
-------------------------------------------------------
What are some reasons to change the configuration register setting? (Choose two.)
**to force the system to ignore the configuration file stored in NVRAM
to monitor password changes
to change the POST sequence
to force the router to boot the IOS from NVRAM
**to force the system into ROM monitor mode
-------------------------------------------------------
A network administrator issues the erase startup-config command on a configured router with the configuration register set to 0x2102 and observes the following output:
Erasing the nvram filesystem will remove all files! Continue? [Confirm]
[OK]
Erase of nvram: complete
If the router unexpectedly loses power after this sequence, what will occur when power is restored?
The router will enter ROM monitor mode upon completion of the power-on self test (POST).
The router will load the last known valid configuration file.
The router will enter Rx-boot mode.
**The router will prompt the user to enter setup mode or to continue without entering setup mode.
-------------------------------------------------------
Which of the following are true regarding the use of login banners? (Choose two.)
The message is only displayed in privileged EXEC mode.
**The message can be seen by everyone who accesses the router.
Good morning is an appropriate message to display.
**The banners should display warning messages.
The banners should identify circuits and other devices connected to the router.
-------------------------------------------------------
Which router component stores the information that is displayed by the show ip route command?
CPU
Flash
NVRAM
**RAM
---------------------------------------------------------
What information can be learned during the initial router bootup? (Choose two.)
the configuration register value
**the number and types of interfaces installed
**the router model and the amount of memory that is available
the amount of memory required to load the IOS and configuration
the number of interfaces with connected cables
-------------------------------------------------------
Which of the following describes CDP? (Choose three.)
**provides information on directly connected Cisco routers that have CDP enabled
**can only be configured between Cisco devices
used for debugging Layer 4 connectivity issues
**should be disabled on non-locally managed ports
presents a potential security risk
------------------------------------------------------
What can a network administrator do to recover from a lost router password?
perform a reload or reset
telnet from another router and issue the show running-config command to view the password
**boot the router to ROM monitor mode and configure the router to ignore NVRAM when it initializes
boot the router to bootROM mode and enter the b command to load the IOS manually
------------------------------------------------------
A network administrator wishes to load a configuration file from a TFTP server into NVRAM on a router. Which of the following methods will create a startup-config file in NVRAM that matches the contents of the configuration file on the TFTP server?
**Copy the configuration file from a TFTP server using the command copy tftp startup-config.
Copy the configuration file from a TFTP server using the command copy< startup-config.
Copy the file to RAM from a console connection using the copy tftp running-config command. Then reload the router to use the new configuration.
Paste the configuration file to the command line of the router while in global configuration mode. Then issue the copy startup-config running-config command.
------------------------------------------------------
Which of the following are primary functions of a router? (Choose two.)
**packet switching
microsegmentation
domain name resolution
**path selection
flow control
------------------------------------------------------
Which of the following are true regarding an interface description? (Choose three.)
It is a message that is displayed at login.
**It does not affect the operation of the router.
It contains the circuit identifiers of the interface by default.
**It could allow support personnel to better understand the scope of an interface problem.
**It could identify the purpose and location of the interface.
It wastes bandwidth and slows down interface problem resolution.
------------------------------------------------------
Which ACL can be applied in the outbound direction of Serial 0/0 on router B in the graphic to allow all IP traffic from LAN A to the Internet, allow Web traffic from LAN B to the Internet, and deny all other traffic to the Internet?
access-list 98 permit 192.168.2.0 0.0.0.255 any
access-list 98 permit tcp 10.90.3.0 0.0.0.255 any eq www
access-list 125 permit ip 192.168.2.0 0.0.0.255 any
access-list 125 permit tcp 10.90.3.0 0.0.0.255 any eq www
access-list 132 permit ip 192.168.2.0 0.0.0.255 any
access-list 132 permit tcp 10.90.3.0 0.0.0.255 any eq www
access-list 132 permit ip any any
**access-list 156 permit ip 192.168.2.0 0.0.0.255 any
**access-list 156 permit ip 10.90.3.0 0.0.0.255 any eq www
-------------------------------------------------------
The following access list has been created to prevent traffic from host 172.23.40.36 from accessing the 192.168.34.0 network.
access-list 44 deny host 172.23.40.36
access-list 44 permit any
Refer to the graphic. Which group of commands will properly place the access list so that the host is denied access only to network 192.168.34.0?
Rome(config)# interface fa0/0
Rome(config-if)# ip access-group 44 in
Rome(config)# interface s0/1
Rome(config-if)# ip access-group 44 out
Tokyo(config)# interface s0/0
Tokyo(config-if)# ip access-group 44 in
**Tokyo(config)# interface fa0/0
**Tokyo(config-if)# ip access-group 44 out
--------------------------------------------------------
Which of the following are true statements regarding IGRP and RIP? (Choose two.)
**IGRP uses a combination of different metrics for path selection.
RIP is a proprietary protocol developed by Cisco.
RIP has the ability to scale to large networks.
**IGRP has the ability to scale to large networks.
--------------------------------------------------
In what order will the initial startup routine of a router locate and load the IOS if the config-register setting is 0x2102 and there are no boot system commands present in the startup-config file?
Flash, ROM, TFTP server
RAM, Flash, NVRAM
Flash, TFTP server, ROM
ROM, TFTP server, Flash
Flash, NVRAM, RAM
**ROM, Flash, TFTP server
--------------------------------------------------
What will occur when the following ACL is applied inbound to both FastEthernet interfaces of Router A in the graphic?
access-list 125 permit tcp 192.168.2.0 0.0.0.255 10.90.3.0 0.0.0.255 eq 23
access-list 125 permit tcp 10.90.3.0 0.0.0.255 192.168.2.0 0.0.0.255 eq 23
access-list 125 permit tcp 192.168.2.0 0.0.0.255 any eq www
**Workstations A and B will be able to Telnet to each other. Workstation A will be allowed to access Web servers on the Internet, while Workstation B will be denied Internet Web access.
Workstations A and B will be able to Telnet to each other. All other traffic will be denied.
The ACL will have no effect because it should be applied in the outbound direction on the FastEthernet interfaces.
The ACL will deny all traffic because of the implied deny ip any any statement at the end of the ACL.
---------------------------------------------------
Which of the following commands will correctly configure an extended ACL? (Choose two).
Router(config)# access-list 18 permit tcp host 192.168.73.3 eq 25
**Router(config)# access-list 102 permit tcp 10.43.0.0 0.0.255.255 any eq 80
**Router(config)# access-list 187 permit tcp host 192.168.42.34 172.29.0.0 0.0.255.255 eq 23
Router(config)# access-list 99 permit host 10.217.32.3
Router(config)# access-list 128 permit tcp host 192.168.100.31 eq 23
----------------------------------------------------
Refer to the graphic. Which command will create a standard ACL that will apply to outbound traffic on interface Fa0/0 of router A and will deny IP traffic from any host on network 172.16.34.0/24 that is destined for network 192.168.5.0/24 while allowing all other IP traffic?
access-list 2 deny 172.16.34.0 0.0.0.0
access-list 2 permit any
**access-list 33 deny 172.16.34.0 0.0.0.255
**access-list 33 permit any
access-list 42 deny 172.16.34.0
access-list 42 permit any
access-list 56 deny tcp 172.16.34.0
access-list 56 permit ip any
------------------------------------------------------
Refer to the network and routing table entries shown in the graphic. How much time will elapse before Router A expects to receive another update from Router B?
5 seconds
13 seconds
**17 seconds
25 seconds
65 seconds
90 seconds
-----------------------------------------------------
Refer to the graphic. Which series of commands will create static routes that will allow Router A and Router B to deliver packets destined for LAN A and LAN B, and direct all other traffic to the Internet?
RouterA(config)# ip route 10.90.3.0 255.255.255.0 192.168.3.2
RouterB(config)# ip route 192.168.2.0 255.255.255.0 192.168.3.1
RouterB(config)# ip route 0.0.0.0 0.0.0.0 s0/0
RouterA(config)# ip route 10.90.3.0 255.255.255.0 192.168.3.2
RouterA(config)# ip route 0.0.0.0 0.0.0.0 192.168.3.2
RouterB(config)# ip route 192.168.2.0 255.255.255.0 192.168.3.1
RouterA(config)# ip route 0.0.0.0 0.0.0.0 192.168.3.2
RouterB(config)# ip route 192.168.2.0 255.255.255.0 192.168.3.1
RouterB(config)# ip route 172.20.20.4 255.255.255.252 s0/0
**RouterA(config)# ip route 0.0.0.0 0.0.0.0 192.168.3.2
**RouterB(config)# ip route 192.168.2.0 255.255.255.0 192.168.3.1
**RouterB(config)# ip route 0.0.0.0 0.0.0.0 s0/0
-----------------------------------------------
Which of the following describe Ethernet and serial interfaces of a router? (Choose two.)
They are enabled by default.
**They may be administratively disabled by using the shutdown command.
**They must be configured with an IP address and subnet mask in order to forward packets.
They must be configured with an IP address and a clockrate in order to forward packets.
They may be administratively disabled by using the no shutdown command.
-----------------------------------------------
Which of the following statements are true regarding routed protocols? (Choose two.)
**They provide enough information in the Layer 3 address to allow a packet to be forwarded from one network to another.
**They carry user data between networks.
They allow routers to share information about networks and their proximity to each other.
They are used by routers to maintain routing tables.
RIP and IGRP are routed protocols.
------------------------------------------------
If a PC does not have network connectivity to a router, which router port can be used to establish communication?
console
**Ethernet
serial
VTY
------------------------------------------------
Router A is directly connected to the networks shown in the graphic and has a default route that points to Router B. All interfaces are active and properly addressed. However, when the workstation on network 172.16.4.0/24 sends a packet to destination address 172.16.201.5, it is discarded by Router A. What can be a reason for this result?
**The ip classless command is not enabled on Router A.
Router B is in a different autonomous system than Router A.
Routers A and B are using different routing protocols.
Router A has no route in its routing table that includes the address 172.16.201.5.
------------------------------------------------
Which of the following prevent successful loading of the Cisco IOS from flash memory? (Choose two.)
**a configuration register set at 0x2102
a missing startup-configuration file
a boot system command not present in the startup-config file
an incorrect configuration register setting
**a boot field set to 2
------------------------------------------------
Which two steps describe how to create a functional physical connection between a router console and a terminal? (Choose two.)
Use a crossover cable to connect the terminal serial port to the router console port.
Use a rollover cable to connect the terminal NIC to the router console port.
**Use an RJ-45 to DB-9 adapter on the terminal serial port to connect to the cable going to the router console.
Use a transceiver to connect a straight-through cable to the router console port.
Use a straight-through cable to connect the router console port to the terminal NIC.
**Use a rollover cable to connect from a terminal serial port to the router console port.
-----------------------------------------------
Refer to the graphic. A network administrator has a console connection to Router A. Pings to Router B are successful, but pings to Routers C and D fail. What is the first step in troubleshooting the problem?
Use the show cdp neighbors detail command from router A to gather information about all Cisco routers in the network.
Use the traceroute command to discover exactly which link in the network is down.
Use an extended ping from router A to each router in the network.
**Use the show interfaces command from a Telnet session on router B to check the connection to router C.
-----------------------------------------------
Based on this partial output of the show ip route command, which routing protocol is configured on the router?
I 172.16.3.0/24 [100/80135] via 172.16.2.2, 00:00:27, Serial0/0
RIP v1
RIP v2
**IGRP
EIGRP
OSPF
IGP
------------------------------------------------
Assuming the following ACL is correctly applied to a router interface, what can be concluded about this set of commands? (Choose two.)
Router(config)# access-list 165 deny tcp 192.28.115.0 0.0.0.255 172.20.0.0 0.0.255.255 eq 23
Router(config)# access-list 165 permit ip any any
This is a standard IP access list that denies network 192.28.115.0 Telnet access to the 172.20.0.0 network.
All Telnet traffic destined for 172.20.0.0 from any network will be denied access.
**Network 192.28.115.0 is denied Telnet access to the 172.20.0.0 network.
Network 172.20.0.0 is denied Telnet access to the 192.28.115.0 network.
**All FTP and HTTP traffic destined for 172.20.0.0 will be permitted access.
------------------------------------------------
What could a Cisco support technician learn from the IOS filename c2600-d-mz.121-3? (Choose three.)
**the format of the file
the RAM memory requirements of the file
**the version number of the file
the size of the file
**the device platform of the file
------------------------------------------------
Which of the following are correct statements verified by the router output shown in the graphic? (Choose two.)
Layer 3 connectivity exists between BigCity and the devices in the Device ID column.
**Layer 2 connectivity exists between BigCity and the devices in the Device ID column.
All devices shown in the Device ID column use the TCP/IP protocol suite.
All devices shown in the Device ID column can be pinged from BigCity.
**All devices listed in the Device ID column are directly connected to BigCity.
------------------------------------------------
What are the results of setting the boot field bits in the configuration register to "0000"? (Choose two.)
The startup-config file will be ignored at bootup.
The router will load the IOS from Flash.
**The router will enter ROM monitor mode upon reload.
The router will enter boot ROM mode and have limited capabilities.
**The administrator can enter the b command to manually boot the IOS.
_________________
Which of the following could describe the devices labeled "?" in the graphic? (Choose three.)
**DCE
**CSU/DSU
LAN switch
**modem
hub
-------------------------------------------------
Router A and Router B have been correctly configured to use RIP as a dynamic routing protocol and all intefaces on Router A and Router B are reporting "interface is up, line protocol is up" status. RIP is then configured on Router C using the following commands:
RouterC(config)# router rip
RouterC(config-router)# network 192.168.4.0
RouterC(config-router)# network 172.16.0.0
If no additional routing is configured on Router A, Router B, and Router C, what will be the result?
**Networks 192.168.12.0/24, 192.168.4.0/24, and 172.16.0.0/16 will be unreachable from Router A.
Router A will have no knowledge of network 192.168.12.0/24, but will have routes to networks 192.168.4.0/24 and 172.16.0.0/16.
All networks shown in the graphic will be reachable by Router A, Router B, and Router C.
Networks 192.168.4.0/24 and 172.16.0.0/16 will be unreachable from Router A and Router B.
--------------------------------------------------------
The following access list has been correctly applied to a router interface:
access-list 52 deny 172.30.65.52
access-list 52 permit any
Which of the following statements are true about this ACL? (Choose three.)
This is an invalid ACL because the wildcard mask is missing from the command.
**A wildcard mask of 0.0.0.0 is assumed for 172.30.65.52.
This is an extended IP access list.
**All traffic from 172.30.65.51 will be permitted.
**This is a standard IP access list.
---------------------------------------------------------
Refer to the graphic. Assuming default metrics are used and the network is fully converged, which path will the IGRP routing protocol use to send a packet from Router A to Router F?
A, D, E, F
**A, B, D, E, F
A, C, D, E, G, F
A, B, D, E, G, F
---------------------------------------------------------
Neither router in the graphic has a host table or DNS available. The interfaces and passwords have been correctly configured. Which of the following commands will initiate a Telnet session? (Choose two.)
ATL> connect CHI
ATL> telnet CHI
**ATL# 192.168.4.2
ATL# connect ATL
**CHI# telnet 192.168.4.1
CHI# telnet ATL
--------------------------------------------------------
What will occur if the command service password-encryption is entered on a router? (Choose two).
It will allow only the user EXEC mode password to be encrypted.
It will set an MD5 hashing algorithm on all unencrypted passwords.
**It will apply a weak encryption to all unencrypted passwords.
It will set the enable secret password to be encrypted.
It will apply an MD5 hashing algorithm to encrypt the console and telnet passwords.
**It will configure the user EXEC mode, telnet, and enable passwords as encrypted.
---------------------------------------------------------
A network administrator must configure a serial interface with an IP address. The configuration must also identify the remote site to which the interface is connected. Which set of commands will meet these requirements?
Chicago(config)# description San Jose T1
Chicago(config)# interface serial0/0
Chicago(config-if)# ip address 192.168.204.9 255.255.255.252
**Chicago(config)# interface serial0/0
**Chicago(config-if)# ip address 192.168.204.9 255.255.255.252
**Chicago(config-if)# description San Jose T1
Chicago(config)# interface serial0/0
Chicago(config-if)# ip address 192.168.204.9 netmask 255.255.255.252
Chicago(config-if)# description San Jose T1
Chicago(config)# interface serial0/0
Chicago(config-if)# ip address 192.168.204.9 255.255.255.252
Chicago(config-if)# remote site San Jose T1
Chicago(config)# interface serial0/0
Chicago(config-if)# ip address 192.168.204.9 255.255.255.252
Chicago(config-if)# interface description San Jose T1
-----------------------------------------------------
A network administrator has enabled RIP on routers B and C in the network diagram. Which of the following commands will prevent RIP updates from being sent to Router A?
A(config)# router rip
A(config-router)# passive-interface S0/0
B(config)# router rip
B(config-router)# network 192.168.25.48
B(config-router)# network 192.168.25.64
A(config)# router rip
A(config-router)# no network 192.168.25.32
**B(config)# router rip
**B(config-router)# passive-interface S0/0
A(config)# no router rip
-----------------------------------------------------
Which of the following describe Telnet on a router? (Choose two.)
**Simultaneous incoming Telnet sessions can be hosted by a router.
Telnet is the most basic testing mechanism available.
A Telnet session can only be initiated in privileged EXEC mode.
**Five separate Telnet lines are specified by the configuration line vty 0 4.
Telnet is classified as a network layer protocol.
--------------------------------------------------
Which commands will show the status and IP address of all interfaces on a router? (Choose two.)
**show protocols
show ip protocols
show version
**show interfaces
show ip ports
---------------------------------------------------
Which router command will generate the router output shown in the graphic?
show arp
show protocols
show interface FastEthernet0/0
show interfaces
**show hardware
---------------------------------------------------
Which of the following are valid boot system commands? (Choose two.)
Router(config)# boot system ram
**Router(config)# boot system rom
Router(config)# boot system IOS flash
Router(config)# boot system flash c2600-d-mz.121-3 192.168.10.5
**Router(config)# boot system tftp c1700-l-mz.131-2 172.16.24.7
---------------------------------------------------
During initial router bootup the following line appears:
"NVRAM invalid, possibly due to write erase."
What are two possible reasons for this result? (Choose two.)
The startup-config file was not saved to RAM before reboot.
The IOS has been erased.
**The router has not been configured.
**The startup-config file cannot be located.
The router will not enter initial configuration dialog.
--------------------------------------------------
While planning an IOS upgrade, the administrator issues the show version command. Based on the output in the graphic, what is the current IOS boot location?
RAM
**NVRAM
Flash
ROM
--------------------------------------------------
Which statements are true regarding setup mode? (Choose three.)
Press Ctrl-z to terminate setup mode.
**Enter a question mark (?) for help at any point.
Press Spacebar to accept the default settings.
Use setup mode to enter complex protocol features.
**Press Enter to accept the default settings.
**Press Ctrl-c to abort configuration dialog.
--------------------------------------------------
Which router components and operations are correctly described? (Choose two.)
ROM - stores the backup configuration file
RAM - loads the operating system
**NVRAM - stores the configuration file
Flash - executes diagnostics at bootup
**POST - runs diagnostics on hardware modules
DRAM - loads the bootstrap
--------------------------------------------------
access-list 199 deny tcp 178.15.0.0 0.0.255.255 any eq 23
access-list 199 permit ip any any
Assuming this ACL is correctly applied to a router interface, which statements describe traffic on the network? (Choose two.)
All FTP traffic from network 178.15.0.0 will be permitted.
**All Telnet traffic destined for network 178.15.0.0 will be denied.
Telnet and FTP will be permitted from all hosts on network 178.15.0.0 to any destination.
**Telnet will not be permitted from any hosts on network 178.15.0.0 to any destination.
Telnet will not be permitted to any host on network 178.15.0.0 from any destination.
------------------------------------------------------
Refer to the graphic. Communication is needed between the LAN connected to the fa0/0 interface of the Kansas router and the fa0/0 interface of the Maine router. All hosts on those LANs also need connectivity to the Internet. Which commands will allow this communication? (Choose three).
**Kansas(config)# ip route 192.168.6.0 255.255.255.0 172.18.64.2
Kansas(config)# ip route 192.168.6.0 255.255.255.0 s0/1
**Kansas(config)# ip route 0.0.0.0 0.0.0.0 s0/1
Maine(config)# ip route 192.168.6.0 255.255.255.0 172.18.64.1
**Maine(config)# ip route 0.0.0.0 0.0.0.0 s0/1
Maine(config)# ip route 172.16.32.0 255.255.255.0 172.18.64.2
-------------------------------------------------------
Due to a security violation, the router passwords must be changed. What information can be learned from the following configuration entries? (Choose two.)
Router(config)# line vty 0 3
Router(config-line)# password c13c0
Router(config-line)# login
The entries specify three Telnet lines for remote access.
**The entries specify four Telnet lines for remote access.
The entries set the console and Telnet password to "c13c0".
Telnet access will be denied because the Telnet configuration is incomplete.
**Access will be permitted for Telnet using "c13c0" as the password.
-------------------------------------------------------
What are some reasons to change the configuration register setting? (Choose two.)
**to force the system to ignore the configuration file stored in NVRAM
to monitor password changes
to change the POST sequence
to force the router to boot the IOS from NVRAM
**to force the system into ROM monitor mode
-------------------------------------------------------
A network administrator issues the erase startup-config command on a configured router with the configuration register set to 0x2102 and observes the following output:
Erasing the nvram filesystem will remove all files! Continue? [Confirm]
[OK]
Erase of nvram: complete
If the router unexpectedly loses power after this sequence, what will occur when power is restored?
The router will enter ROM monitor mode upon completion of the power-on self test (POST).
The router will load the last known valid configuration file.
The router will enter Rx-boot mode.
**The router will prompt the user to enter setup mode or to continue without entering setup mode.
-------------------------------------------------------
Which of the following are true regarding the use of login banners? (Choose two.)
The message is only displayed in privileged EXEC mode.
**The message can be seen by everyone who accesses the router.
Good morning is an appropriate message to display.
**The banners should display warning messages.
The banners should identify circuits and other devices connected to the router.
-------------------------------------------------------
Which router component stores the information that is displayed by the show ip route command?
CPU
Flash
NVRAM
**RAM
---------------------------------------------------------
What information can be learned during the initial router bootup? (Choose two.)
the configuration register value
**the number and types of interfaces installed
**the router model and the amount of memory that is available
the amount of memory required to load the IOS and configuration
the number of interfaces with connected cables
-------------------------------------------------------
Which of the following describes CDP? (Choose three.)
**provides information on directly connected Cisco routers that have CDP enabled
**can only be configured between Cisco devices
used for debugging Layer 4 connectivity issues
**should be disabled on non-locally managed ports
presents a potential security risk
------------------------------------------------------
What can a network administrator do to recover from a lost router password?
perform a reload or reset
telnet from another router and issue the show running-config command to view the password
**boot the router to ROM monitor mode and configure the router to ignore NVRAM when it initializes
boot the router to bootROM mode and enter the b command to load the IOS manually
------------------------------------------------------
A network administrator wishes to load a configuration file from a TFTP server into NVRAM on a router. Which of the following methods will create a startup-config file in NVRAM that matches the contents of the configuration file on the TFTP server?
**Copy the configuration file from a TFTP server using the command copy tftp startup-config.
Copy the configuration file from a TFTP server using the command copy
Copy the file to RAM from a console connection using the copy tftp running-config command. Then reload the router to use the new configuration.
Paste the configuration file to the command line of the router while in global configuration mode. Then issue the copy startup-config running-config command.
------------------------------------------------------
Which of the following are primary functions of a router? (Choose two.)
**packet switching
microsegmentation
domain name resolution
**path selection
flow control
------------------------------------------------------
Which of the following are true regarding an interface description? (Choose three.)
It is a message that is displayed at login.
**It does not affect the operation of the router.
It contains the circuit identifiers of the interface by default.
**It could allow support personnel to better understand the scope of an interface problem.
**It could identify the purpose and location of the interface.
It wastes bandwidth and slows down interface problem resolution.
------------------------------------------------------
Which ACL can be applied in the outbound direction of Serial 0/0 on router B in the graphic to allow all IP traffic from LAN A to the Internet, allow Web traffic from LAN B to the Internet, and deny all other traffic to the Internet?
access-list 98 permit 192.168.2.0 0.0.0.255 any
access-list 98 permit tcp 10.90.3.0 0.0.0.255 any eq www
access-list 125 permit ip 192.168.2.0 0.0.0.255 any
access-list 125 permit tcp 10.90.3.0 0.0.0.255 any eq www
access-list 132 permit ip 192.168.2.0 0.0.0.255 any
access-list 132 permit tcp 10.90.3.0 0.0.0.255 any eq www
access-list 132 permit ip any any
**access-list 156 permit ip 192.168.2.0 0.0.0.255 any
**access-list 156 permit ip 10.90.3.0 0.0.0.255 any eq www
-------------------------------------------------------
The following access list has been created to prevent traffic from host 172.23.40.36 from accessing the 192.168.34.0 network.
access-list 44 deny host 172.23.40.36
access-list 44 permit any
Refer to the graphic. Which group of commands will properly place the access list so that the host is denied access only to network 192.168.34.0?
Rome(config)# interface fa0/0
Rome(config-if)# ip access-group 44 in
Rome(config)# interface s0/1
Rome(config-if)# ip access-group 44 out
Tokyo(config)# interface s0/0
Tokyo(config-if)# ip access-group 44 in
**Tokyo(config)# interface fa0/0
**Tokyo(config-if)# ip access-group 44 out
--------------------------------------------------------
Which of the following are true statements regarding IGRP and RIP? (Choose two.)
**IGRP uses a combination of different metrics for path selection.
RIP is a proprietary protocol developed by Cisco.
RIP has the ability to scale to large networks.
**IGRP has the ability to scale to large networks.
--------------------------------------------------
In what order will the initial startup routine of a router locate and load the IOS if the config-register setting is 0x2102 and there are no boot system commands present in the startup-config file?
Flash, ROM, TFTP server
RAM, Flash, NVRAM
Flash, TFTP server, ROM
ROM, TFTP server, Flash
Flash, NVRAM, RAM
**ROM, Flash, TFTP server
--------------------------------------------------
What will occur when the following ACL is applied inbound to both FastEthernet interfaces of Router A in the graphic?
access-list 125 permit tcp 192.168.2.0 0.0.0.255 10.90.3.0 0.0.0.255 eq 23
access-list 125 permit tcp 10.90.3.0 0.0.0.255 192.168.2.0 0.0.0.255 eq 23
access-list 125 permit tcp 192.168.2.0 0.0.0.255 any eq www
**Workstations A and B will be able to Telnet to each other. Workstation A will be allowed to access Web servers on the Internet, while Workstation B will be denied Internet Web access.
Workstations A and B will be able to Telnet to each other. All other traffic will be denied.
The ACL will have no effect because it should be applied in the outbound direction on the FastEthernet interfaces.
The ACL will deny all traffic because of the implied deny ip any any statement at the end of the ACL.
---------------------------------------------------
Which of the following commands will correctly configure an extended ACL? (Choose two).
Router(config)# access-list 18 permit tcp host 192.168.73.3 eq 25
**Router(config)# access-list 102 permit tcp 10.43.0.0 0.0.255.255 any eq 80
**Router(config)# access-list 187 permit tcp host 192.168.42.34 172.29.0.0 0.0.255.255 eq 23
Router(config)# access-list 99 permit host 10.217.32.3
Router(config)# access-list 128 permit tcp host 192.168.100.31 eq 23
----------------------------------------------------
Refer to the graphic. Which command will create a standard ACL that will apply to outbound traffic on interface Fa0/0 of router A and will deny IP traffic from any host on network 172.16.34.0/24 that is destined for network 192.168.5.0/24 while allowing all other IP traffic?
access-list 2 deny 172.16.34.0 0.0.0.0
access-list 2 permit any
**access-list 33 deny 172.16.34.0 0.0.0.255
**access-list 33 permit any
access-list 42 deny 172.16.34.0
access-list 42 permit any
access-list 56 deny tcp 172.16.34.0
access-list 56 permit ip any
------------------------------------------------------
Refer to the network and routing table entries shown in the graphic. How much time will elapse before Router A expects to receive another update from Router B?
5 seconds
13 seconds
**17 seconds
25 seconds
65 seconds
90 seconds
-----------------------------------------------------
Refer to the graphic. Which series of commands will create static routes that will allow Router A and Router B to deliver packets destined for LAN A and LAN B, and direct all other traffic to the Internet?
RouterA(config)# ip route 10.90.3.0 255.255.255.0 192.168.3.2
RouterB(config)# ip route 192.168.2.0 255.255.255.0 192.168.3.1
RouterB(config)# ip route 0.0.0.0 0.0.0.0 s0/0
RouterA(config)# ip route 10.90.3.0 255.255.255.0 192.168.3.2
RouterA(config)# ip route 0.0.0.0 0.0.0.0 192.168.3.2
RouterB(config)# ip route 192.168.2.0 255.255.255.0 192.168.3.1
RouterA(config)# ip route 0.0.0.0 0.0.0.0 192.168.3.2
RouterB(config)# ip route 192.168.2.0 255.255.255.0 192.168.3.1
RouterB(config)# ip route 172.20.20.4 255.255.255.252 s0/0
**RouterA(config)# ip route 0.0.0.0 0.0.0.0 192.168.3.2
**RouterB(config)# ip route 192.168.2.0 255.255.255.0 192.168.3.1
**RouterB(config)# ip route 0.0.0.0 0.0.0.0 s0/0
-----------------------------------------------
Which of the following describe Ethernet and serial interfaces of a router? (Choose two.)
They are enabled by default.
**They may be administratively disabled by using the shutdown command.
**They must be configured with an IP address and subnet mask in order to forward packets.
They must be configured with an IP address and a clockrate in order to forward packets.
They may be administratively disabled by using the no shutdown command.
-----------------------------------------------
Which of the following statements are true regarding routed protocols? (Choose two.)
**They provide enough information in the Layer 3 address to allow a packet to be forwarded from one network to another.
**They carry user data between networks.
They allow routers to share information about networks and their proximity to each other.
They are used by routers to maintain routing tables.
RIP and IGRP are routed protocols.
------------------------------------------------
If a PC does not have network connectivity to a router, which router port can be used to establish communication?
console
**Ethernet
serial
VTY
------------------------------------------------
Router A is directly connected to the networks shown in the graphic and has a default route that points to Router B. All interfaces are active and properly addressed. However, when the workstation on network 172.16.4.0/24 sends a packet to destination address 172.16.201.5, it is discarded by Router A. What can be a reason for this result?
**The ip classless command is not enabled on Router A.
Router B is in a different autonomous system than Router A.
Routers A and B are using different routing protocols.
Router A has no route in its routing table that includes the address 172.16.201.5.
------------------------------------------------
Which of the following prevent successful loading of the Cisco IOS from flash memory? (Choose two.)
**a configuration register set at 0x2102
a missing startup-configuration file
a boot system command not present in the startup-config file
an incorrect configuration register setting
**a boot field set to 2
------------------------------------------------
Which two steps describe how to create a functional physical connection between a router console and a terminal? (Choose two.)
Use a crossover cable to connect the terminal serial port to the router console port.
Use a rollover cable to connect the terminal NIC to the router console port.
**Use an RJ-45 to DB-9 adapter on the terminal serial port to connect to the cable going to the router console.
Use a transceiver to connect a straight-through cable to the router console port.
Use a straight-through cable to connect the router console port to the terminal NIC.
**Use a rollover cable to connect from a terminal serial port to the router console port.
-----------------------------------------------
Refer to the graphic. A network administrator has a console connection to Router A. Pings to Router B are successful, but pings to Routers C and D fail. What is the first step in troubleshooting the problem?
Use the show cdp neighbors detail command from router A to gather information about all Cisco routers in the network.
Use the traceroute command to discover exactly which link in the network is down.
Use an extended ping from router A to each router in the network.
**Use the show interfaces command from a Telnet session on router B to check the connection to router C.
-----------------------------------------------
Based on this partial output of the show ip route command, which routing protocol is configured on the router?
I 172.16.3.0/24 [100/80135] via 172.16.2.2, 00:00:27, Serial0/0
RIP v1
RIP v2
**IGRP
EIGRP
OSPF
IGP
------------------------------------------------
Assuming the following ACL is correctly applied to a router interface, what can be concluded about this set of commands? (Choose two.)
Router(config)# access-list 165 deny tcp 192.28.115.0 0.0.0.255 172.20.0.0 0.0.255.255 eq 23
Router(config)# access-list 165 permit ip any any
This is a standard IP access list that denies network 192.28.115.0 Telnet access to the 172.20.0.0 network.
All Telnet traffic destined for 172.20.0.0 from any network will be denied access.
**Network 192.28.115.0 is denied Telnet access to the 172.20.0.0 network.
Network 172.20.0.0 is denied Telnet access to the 192.28.115.0 network.
**All FTP and HTTP traffic destined for 172.20.0.0 will be permitted access.
------------------------------------------------
What could a Cisco support technician learn from the IOS filename c2600-d-mz.121-3? (Choose three.)
**the format of the file
the RAM memory requirements of the file
**the version number of the file
the size of the file
**the device platform of the file
------------------------------------------------
Which of the following are correct statements verified by the router output shown in the graphic? (Choose two.)
Layer 3 connectivity exists between BigCity and the devices in the Device ID column.
**Layer 2 connectivity exists between BigCity and the devices in the Device ID column.
All devices shown in the Device ID column use the TCP/IP protocol suite.
All devices shown in the Device ID column can be pinged from BigCity.
**All devices listed in the Device ID column are directly connected to BigCity.
------------------------------------------------
What are the results of setting the boot field bits in the configuration register to "0000"? (Choose two.)
The startup-config file will be ignored at bootup.
The router will load the IOS from Flash.
**The router will enter ROM monitor mode upon reload.
The router will enter boot ROM mode and have limited capabilities.
**The administrator can enter the b command to manually boot the IOS.
_________________
sobota 4. srpna 2007
Psytrance - Best software
Synths for psytrance sounds:
- Predator 1.0.1b
- Albino 3.0.2
- FireBird 1.2.1
- Vanguard
- SuperWave P8
- Absynth, powerful vst and has really cool atmospheric psy sounds
- Massive, the name says it all, must have, trust me;) (native)
- Nexus, one of the warmest softhsynths around (refx)
- FM8, massive-style monster(native)
- FX, camelphat, camelspace, camelcrusher, glitch, pudding,predatohm(disto)
- Blue (rob Papen)
- Discovery
- D'cota
- Korg legacy cell !!!
- Trilogy (spectraphonics)
- Atmosphere (spectraphonics)
- Crystal (pads)
[quote]Massive and FM8 are amazing synths... don't know for psymuze but they do the trick for me
- Predator 1.0.1b
- Albino 3.0.2
- FireBird 1.2.1
- Vanguard
- SuperWave P8
- Absynth, powerful vst and has really cool atmospheric psy sounds
- Massive, the name says it all, must have, trust me;) (native)
- Nexus, one of the warmest softhsynths around (refx)
- FM8, massive-style monster(native)
- FX, camelphat, camelspace, camelcrusher, glitch, pudding,predatohm(disto)
- Blue (rob Papen)
- Discovery
- D'cota
- Korg legacy cell !!!
- Trilogy (spectraphonics)
- Atmosphere (spectraphonics)
- Crystal (pads)
[quote]Massive and FM8 are amazing synths... don't know for psymuze but they do the trick for me
středa 1. srpna 2007
Routery - BGP
Border Gateway Protocol (BGP) je dynamický směrovací protokol používaný pro směrování mezi autonomními systémy (AS). Je základem propojení sítí různých ISP v peeringových uzlech.
Směrování mezi autonomními systémy má charakteristické požadavky, které se nevyskytují v interním směrování. Směrovací tabulky obsahují stovky tisíc záznamů, nejdůležitějším kritériem nebývá vzdálenost, ale posuzují se nastavitelné parametry zohledňující například cenu a dodatečná pravidla aplikovaná v závislosti na zdroji, cíli, seznamu tranzitních autonomních systémů a dalších atributech.
Vzhledem k velkému počtu záznamu se v případě změn v topologii vyměňují pouze informace o změnách, nikoliv celé směrovací tabulky jako je tomu v případě protokolu RIP.
Směrování mezi autonomními systémy má charakteristické požadavky, které se nevyskytují v interním směrování. Směrovací tabulky obsahují stovky tisíc záznamů, nejdůležitějším kritériem nebývá vzdálenost, ale posuzují se nastavitelné parametry zohledňující například cenu a dodatečná pravidla aplikovaná v závislosti na zdroji, cíli, seznamu tranzitních autonomních systémů a dalších atributech.
Vzhledem k velkému počtu záznamu se v případě změn v topologii vyměňují pouze informace o změnách, nikoliv celé směrovací tabulky jako je tomu v případě protokolu RIP.
Routery - OSPF
Open Shortest Path First
Open Shortest Path First (OSPF) je adaptivní hierarchický distribuovaný routovací protokol, provádějící změny v routovacích tabulkách na základě změny stavu v síti. Jedná se o nejpoužívanější routovací protokol uvnitř autonomních systémů.
Routery, používající tento protokol, si v pravidelných krátkých intervalech zvláštními zprávami (ECHO) kontrolují spojení se svými sousedními routery. Při zjištění jakékoliv změny zasílá oznámení všem routerům v síti, ty si pak podle nové informace přepočítají nové cesty v síti a podle toho upraví routovací tabulky.
Výpočet nejkratších cest se provádí Dijkstrovým algoritmem.
Dalším vylepšením tohoto protokolu je rozdělení autonomního systému na několik oblastí (proto hierarchický), ve kterých si routery vzájemně vyměnují sdělení o změnách v síti, ale mimo svou oblast je neposílají. O výměnu souhrnných informací mezi oblastmi se starají hraniční routery. Touto technikou se zamezuje zahlcování rozlehlých sítí informacemi o změnách při velkém počtu routerů v autonomním systému.
(článek z wikipedia.cz)
Open Shortest Path First (OSPF) je adaptivní hierarchický distribuovaný routovací protokol, provádějící změny v routovacích tabulkách na základě změny stavu v síti. Jedná se o nejpoužívanější routovací protokol uvnitř autonomních systémů.
Routery, používající tento protokol, si v pravidelných krátkých intervalech zvláštními zprávami (ECHO) kontrolují spojení se svými sousedními routery. Při zjištění jakékoliv změny zasílá oznámení všem routerům v síti, ty si pak podle nové informace přepočítají nové cesty v síti a podle toho upraví routovací tabulky.
Výpočet nejkratších cest se provádí Dijkstrovým algoritmem.
Dalším vylepšením tohoto protokolu je rozdělení autonomního systému na několik oblastí (proto hierarchický), ve kterých si routery vzájemně vyměnují sdělení o změnách v síti, ale mimo svou oblast je neposílají. O výměnu souhrnných informací mezi oblastmi se starají hraniční routery. Touto technikou se zamezuje zahlcování rozlehlých sítí informacemi o změnách při velkém počtu routerů v autonomním systému.
(článek z wikipedia.cz)
Přihlásit se k odběru:
Komentáře (Atom)